Server certificates: These certificates identify a server (computer) and contain the host name or IP address. They are used for one- or two-layer SSL to ensure secure communication of data over a network. Because digital certificates are standard in data exchange and security protocols for digital ID systems (including the TLS encryption measures described above, as well as smartcard- and mobile-based authentication), a country’s PKI is landscape is a common building block for many ID systems.
- General Conclusions…
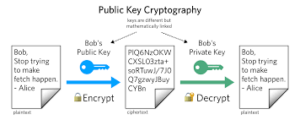
- PKI is a system/standard/protocol of secured communication between several entities within a network
- public keys are to encrypt, private keys are to decrypt. THAT’S why leaking your private key is effed. You’re basically giving out the solution to a puzzle you don’t want anyone else to solve!
- interesting, so you can encrypt using a private key as well – but ONLY FOR DIGITAL SIGNATURES! you encrypt your signature, someone decrypts it with a public key – if its successful, then they confirm your identity because it PROVES you have the private key
- TLS and SSL are encryption algorithms PKI uses
- Connections…
- DKIM TXT record you set up in your DNS, that’s essentially a public key; DKIM uses cryptography to verify the authenticity of an email and prevent spam. DKIM uses an encrypted header to add a digital signature to the email, which verifies that it was sent and authorized by the domain’s owner
THINGS TO LOOK INTO…
Certificate Authorizations (CA’s)
Certificate Hierarchies
How certificates are deployed across a domain/network
ADDITIONAL READINGS…
https://id4d.worldbank.org/guide/digital-certificates-and-pki
https://support.apple.com/guide/deployment/intro-to-certificate-management-depb5eff8914/web
https://support.apple.com/guide/deployment/intro-to-certificate-management-depb5eff8914/web